Single Sign-On (SSO) lets users access multiple apps with one set of credentials—but when something breaks, it can slow things down for everyone.
Common issues like login errors, misconfigured settings, or security mismatches can sometimes pop up. Knowing how to spot and troubleshoot these things helps keep everything running smoothly on your Jotform Enterprise server.
Issues When Setting Up SSO
If SSO isn’t set up properly, it can lead to a range of issues—from preventing users from logging in and and system hiccups to potential security concerns. It can slow down your team and create unnecessary confusion. The good news is that most of these things are easy to fix. Once they’re resolved, everything should run more smoothly.
Below are some of the most common SSO issues you might run into.
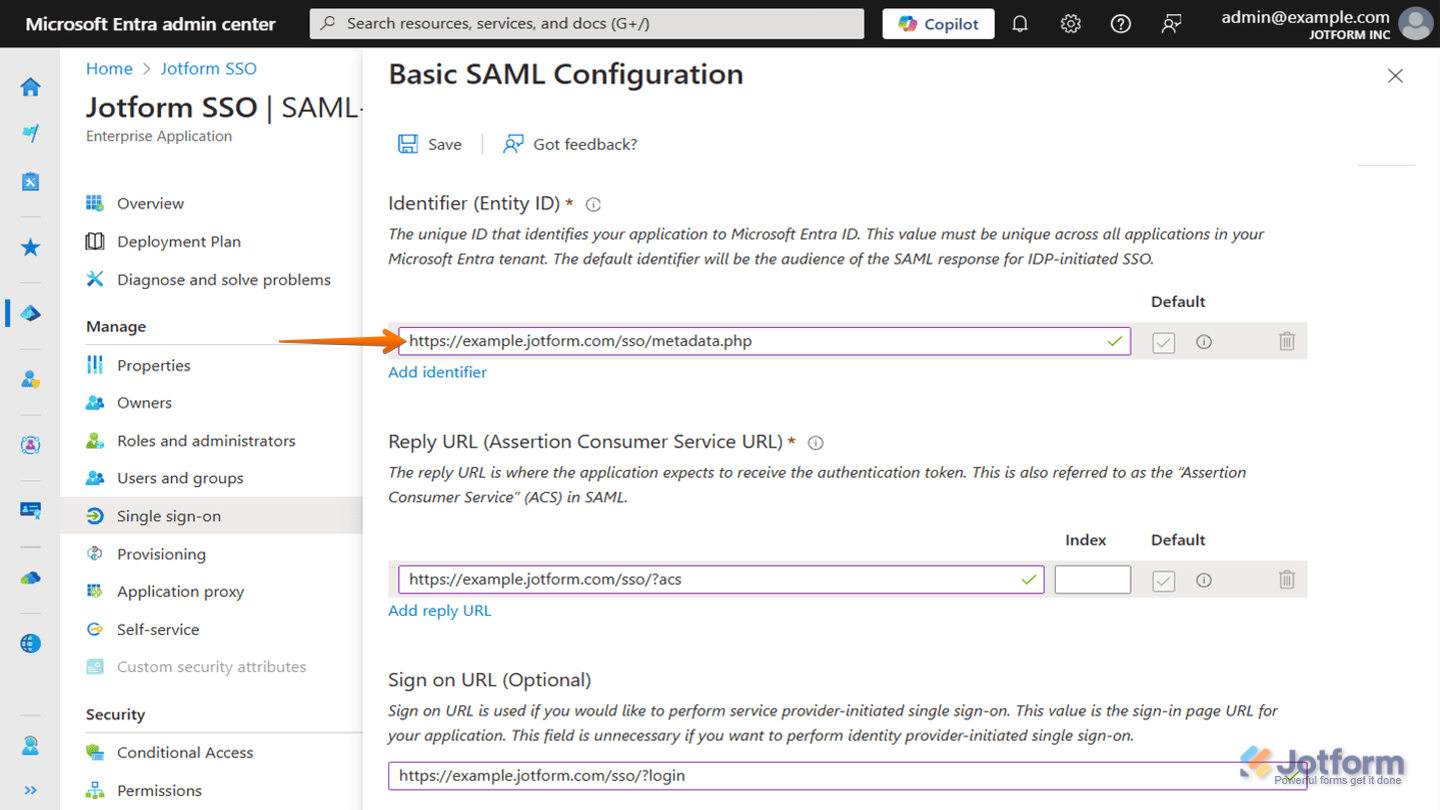
Identifier Settings Mismatch
This usually comes up when there’s an issue with your Identifier settings (also known as the Entity ID). If the URL you use in the SAML configuration doesn’t include the full protocol, like https://, SSO won’t work properly.
Here’s what a correct SAML setup looks like using Microsoft Entra ID for SSO:
https://example.jotform.com/sso/metadata.php
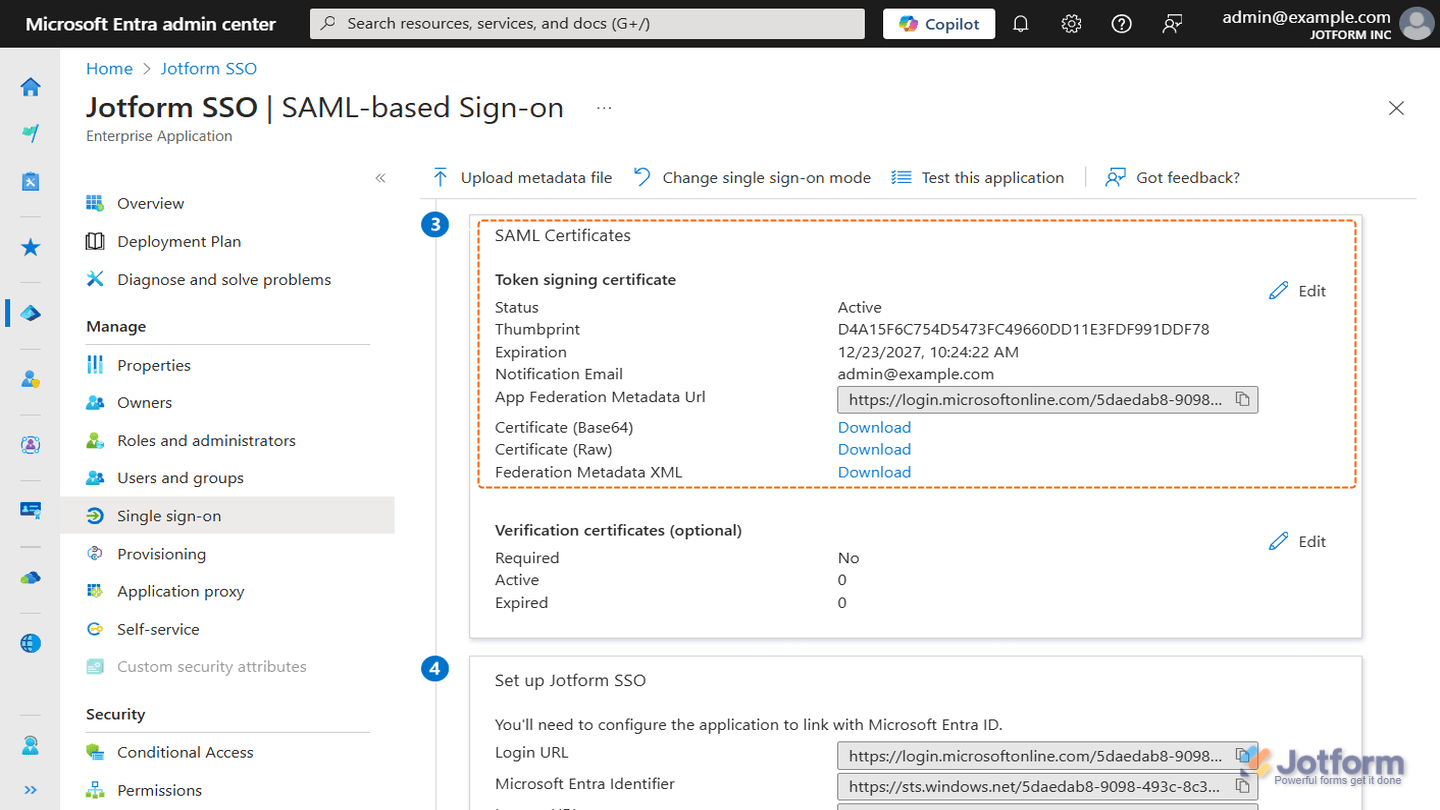
Certificate Expired
The SSO login process relies on two certificates—one from Jotform and one from your Identity Provider (IdP). If you see an Expired Certificate error, it’s usually the IdP’s certificate that needs attention. Some IdPs don’t renew certificates automatically, so you’ll need to generate a new one and upload it to your Jotform Enterprise settings.
We’re focusing on the IdP’s certificate here, since even if Jotform’s certificate expires, you’ll still be able to access your Enterprise server and reach out to Enterprise Support if needed. Here’s an example of the SAML certificates in Microsoft Entra ID for SSO:
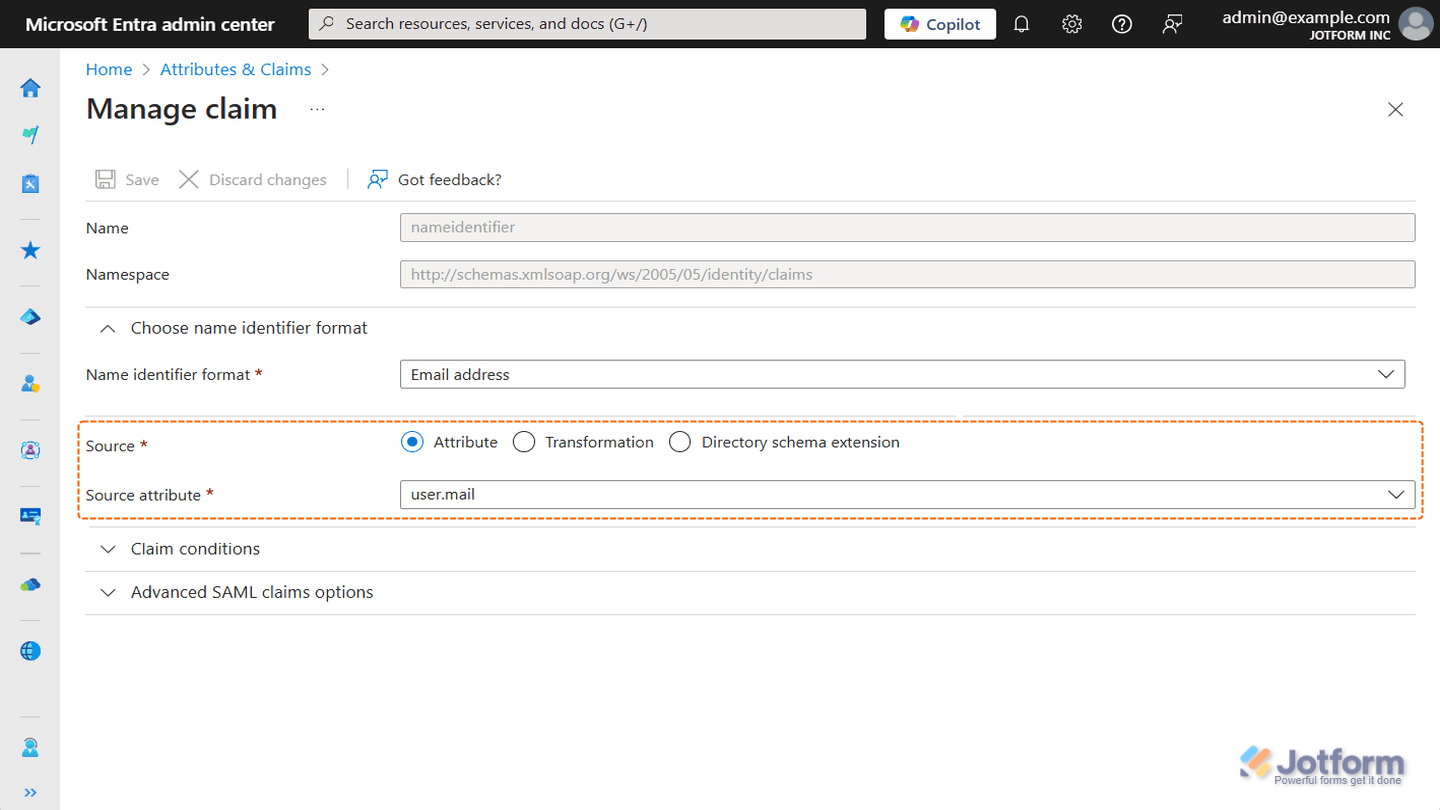
SSO Email Not Found
For SSO to work properly in Jotform, every user in your IdP needs to have an email address. This email identifies the user and allows them to log in. You can pass it through the Name ID format or include it as a separate claim—whatever works best for your setup. The key is making sure each user has a valid email linked to their account.
In Microsoft Entra ID, for example, the Source and Source Attribute typically point to the user’s email as the Unique User Identifier:
Note
This can also cause users to be logged out unexpectedly, even if they’re already signed in. It should stop happening once the Name ID is set up correctly in your IdP.
Issues When Logging Out with SSO Enabled
SSO makes it easy to log in across different apps, but logging out doesn’t always work the same way. Ending a session in one app doesn’t always end it in others. These logout issues can cause confusion—or worse, with sessions open longer than they should be.
Below are some of the most common issues you might run into when logging out with SSO enabled.
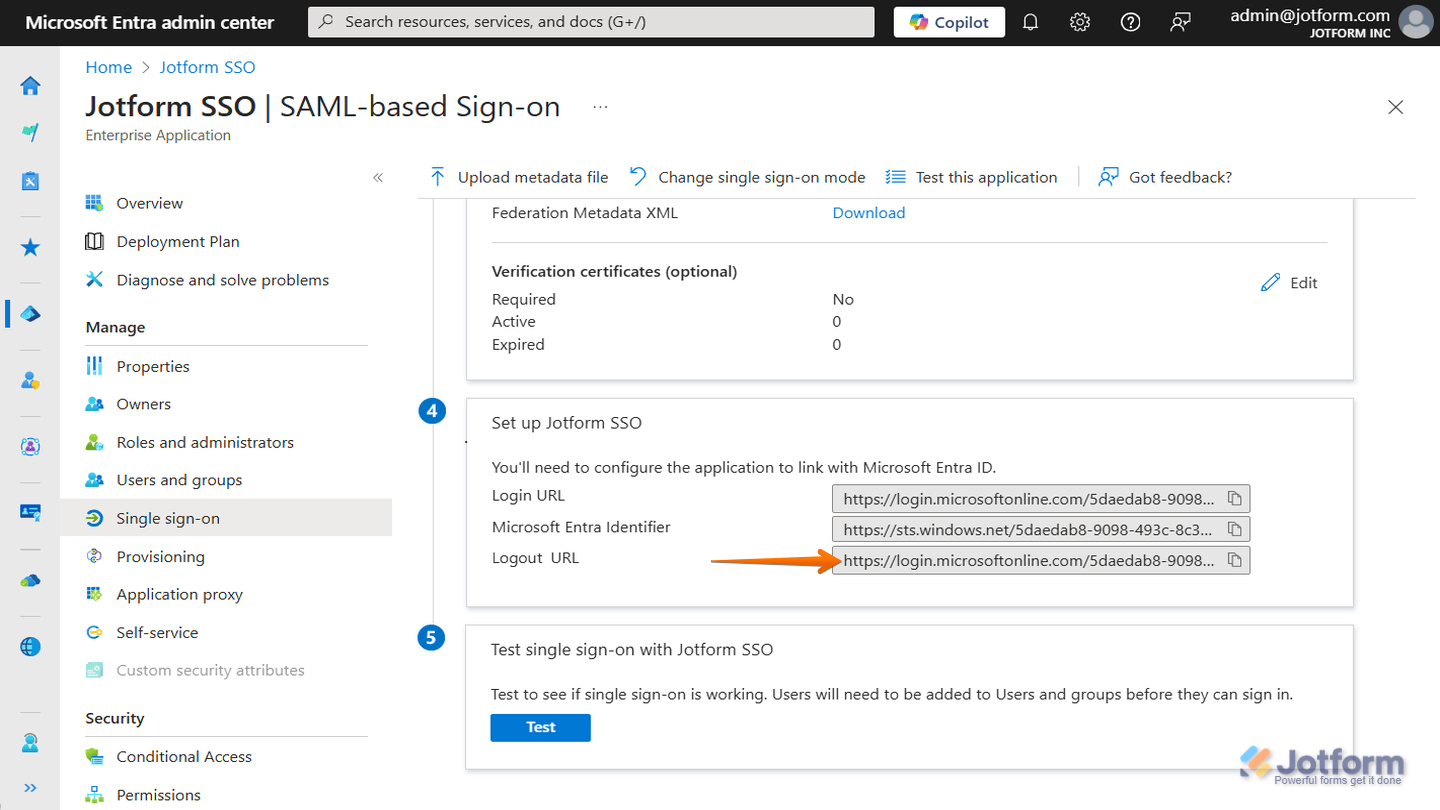
Incorrect SLO URL
This usually happens when the Single Logout (SLO) URL in your Jotform Enterprise settings isn’t set up correctly. If it’s wrong, users can get stuck in a redirect loop and never fully log out. In most cases, the SLO URL is the same as your Jotform SSO URL. You can find it in your account’s Single Sign-On settings. For a quick how-to, check out our guide on How to Obtain Service Provider Metadata from Jotform Enterprise. Here’s an example of the correct SSO Logout URL:
Google SSO Doesn’t Support SLO
IdPs support SLO, but Google SSO doesn’t. If you’re using Google SSO, just leave the SLO URL field blank in your Jotform Enterprise settings. After that, contact Enterprise Support to set up a custom logout page for your server. It’ll look something like this:
Issues When Logging In with SSO Enabled
Sometimes users have trouble logging in to a Jotform Enterprise server when SSO is turned on. This usually happens because the SLO URL is either set up wrong or not supported by the IdP. Sorting this out helps keep the login experience smooth for everyone.
Here’s a break down of what causes these issues.
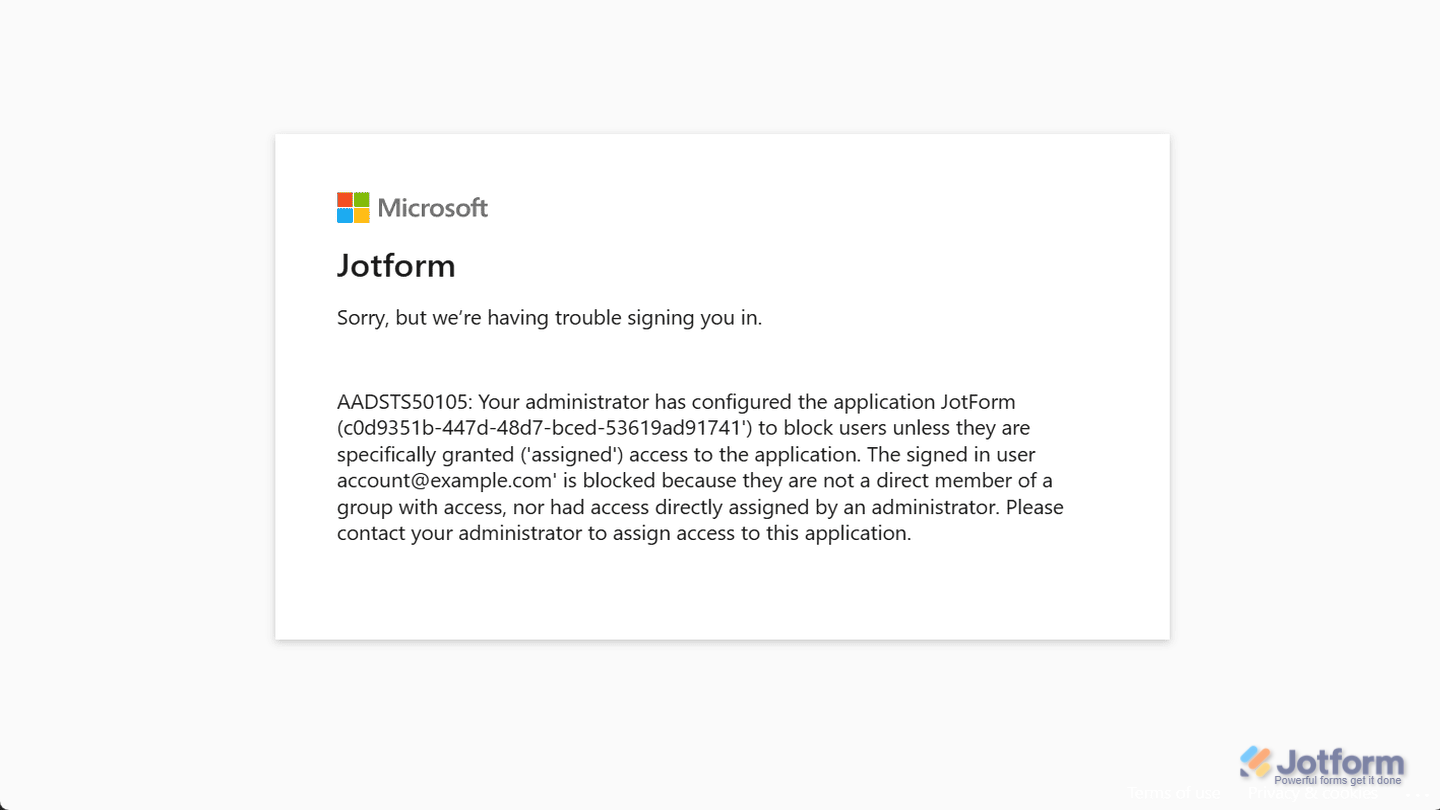
The Signed-In User Is Blocked
Turning on SSO isn’t just about adding users to your Jotform Enterprise server—you also need to make sure they’re set up properly in your SSO provider. If that part’s missed, new users won’t be able to log in. Here’s an example of the error message they might see if they’re not added to your SSO provider:
Application with Identifier Was Not Found
If your Enterprise users see an error saying metadata information is missing from the directory, it usually means that something wasn’t entered properly in the Admin Console. This often comes up during the first SSO setup or after changes to your custom domain or slug. To avoid this, SSO should be turned off before making domain updates. Once the changes are done, update the metadata in your SSO settings and turn SSO back on. Here’s the example of the error:
Note
We’re working to improve this experience in Jotform Enterprise. In the meantime, if you update your domain or slug while SSO is enabled, your server may become temporarily inaccessible. Reach out to Enterprise Support for help.
Issues Related to SSO Attributes
SSO makes it easier to log in to different apps with just one set of credentials. But if any of the required attributes are missing or set up wrong, it can cause login issues and make it harder to manage your Enterprise forms. Getting your SSO attributes right helps everything run smoothly and gives users a better experience.
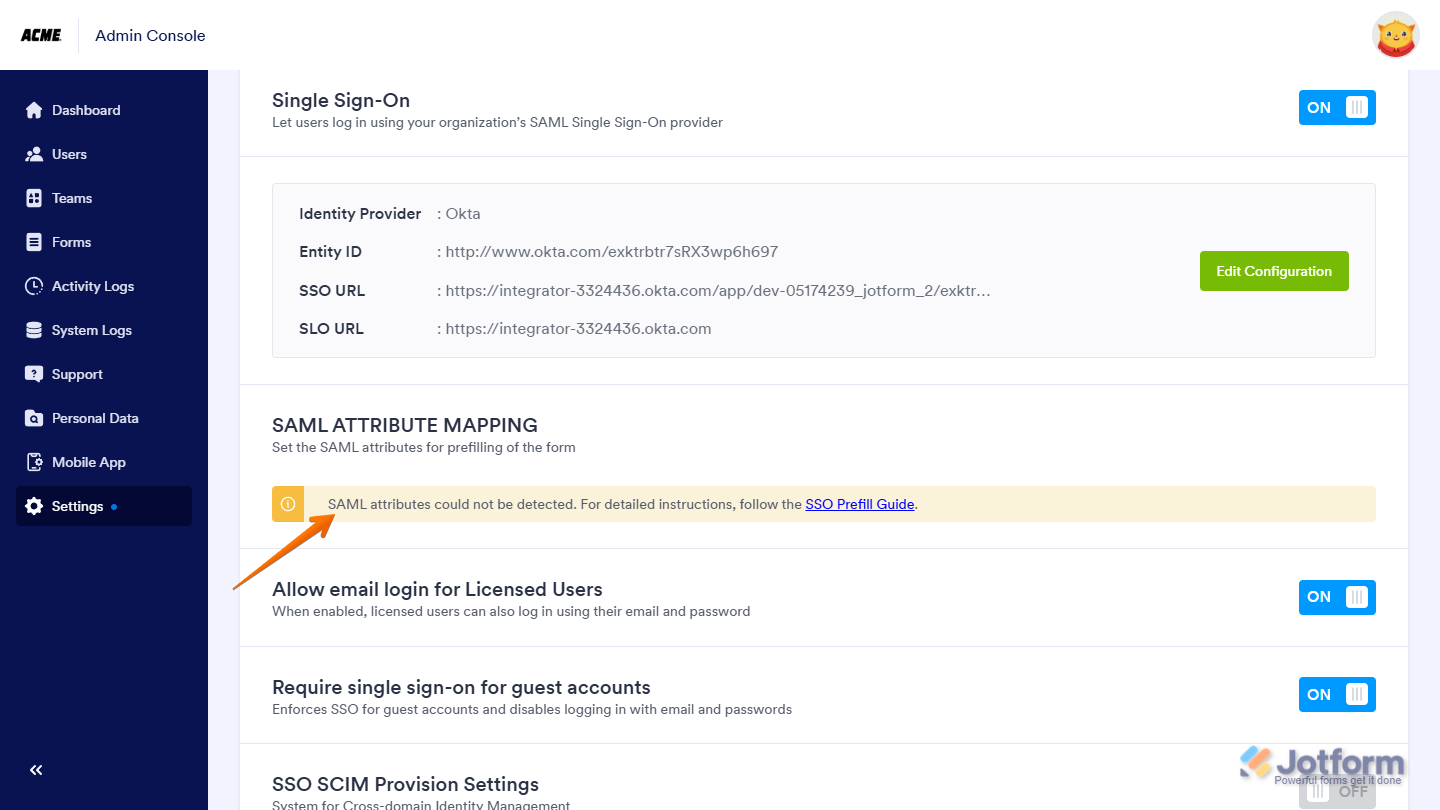
SAML Attributes Could Not Be Detected
With Jotform Enterprise, you can map your SAML Attributes right in your Enterprise Server settings. If something’s off and the system can’t detect those attributes, you’ll see a warning on the settings page like in the example below:
To get things working, make sure SSO Prefill is set up correctly. For a full breakdown of how to do it, head over to our guide on How to Enable SSO Prefill.
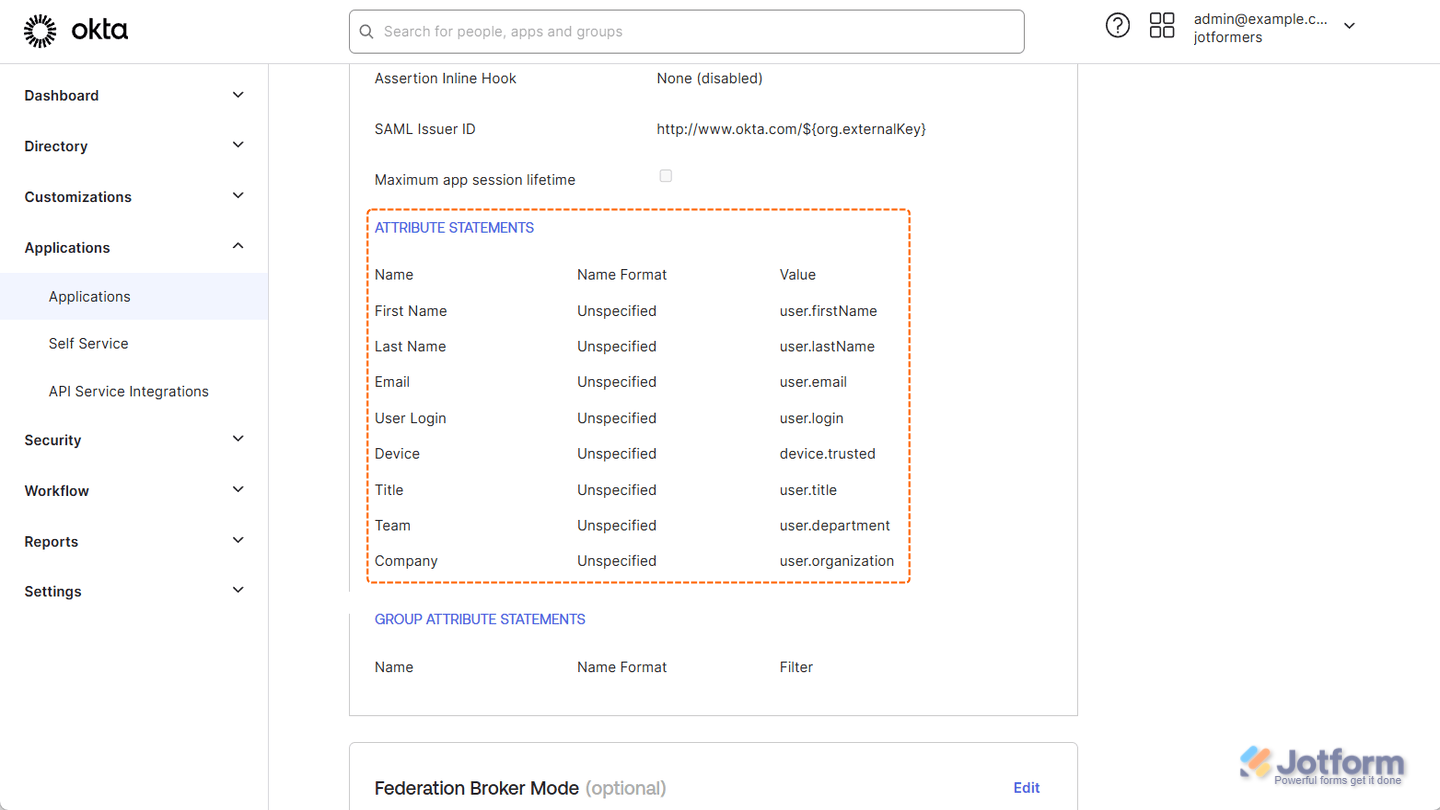
Attributes Not Appearing in Attribute Mapping
IdPs like Okta offer a variety of attributes you can claim. But if an attribute doesn’t have a value assigned to it, it won’t be shown in your SSO settings in the Jotform Enterprise Admin Console. To make sure everything shows up as expected, double-check that each attribute has a valid value and is properly added to your SSO application. Here’s a quick example of how it looks in Okta:
Note
After adding attribute values in the Admin Console, log out and then log back in to make sure the updates take effect. Attribute values are pulled in during login, so this step helps apply the changes properly.

Send Comment: